💡 : It is possible to listen to this article! Find the audio at the bottom of the page 🎧
In the past, software was on premise, there were not many of them, and some did not even have a connection with the internet.
Today, each employee has a large number of applications (it is difficult to give an average because it depends on the size of the company and the sector of activity), and access management becomes a headache for the IT department.
Cybercrime is very high, and each access granted becomes an entry point into the company if not configured correctly.
For example, can you assure today that there are no open accesses with departed users? Or can you be sure that each user is properly configured with the correct security group and the resulting accesses?
What is Identity Governance and Administration?
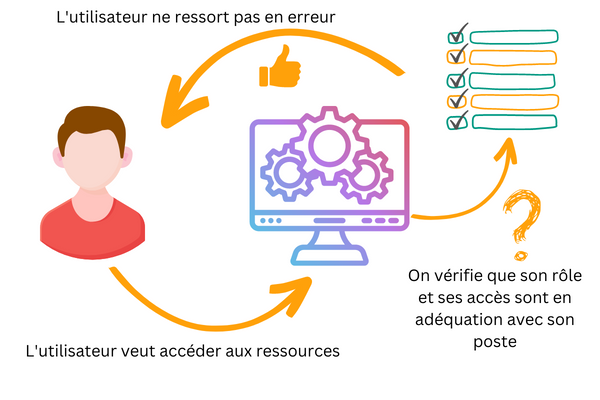
Identity Governance and Administration ensures users access to information system resources (systems, applications, and data) in accordance with their role and professional needs, with the appropriate level of access.
This improves visibility into privileges, controls and manages identities and access, provides traceability of actions, and manages the user lifecycle.
IGA works as follows: it centralizes information from multiple sources (HR, applications, IT) and identifies entitlements, then ensures compliance.
An IT IGA solution supports SaaS or on-premise software, rights and access must be managed precisely.
In what context does IGA position itself?
As I presented in the introduction, companies have become highly digitized, and the Covid period has marked a multiplication of SaaS solutions.
Cyberattacks are constant and increasing, and internal security vulnerabilities are multiplying with the increase in applications per user. The processes of IT departments are becoming more complex.
SaaS solutions are easy to install within a company, which can lead to shadow IT if this practice is carried out outside the IT department's purview. The rights granted are often very broad, and license management is difficult to maintain.
BYOD, Bring Your Own Device, is popular with users but requires great control by the IT department.
IT budgets tend to increase, but a fine strategy is needed to balance user needs (with a focus on productivity) on the one hand, and security needs on the other, in order to supervise the IS.
Finally, from a security standpoint, audits are required in several sectors, and compliance must be achieved, which necessitates conducting account reviews and having a precise view of the information system at a specific point in time.
Briefly, what is an identity governance and administration tool for?
This allows you to:
- To quickly open and close a user's access rights
- Track and control user access
- detect and prevent inappropriate access
- give the right users the right access and the right rights
- Reduce risk and ensure compliance.
- save time in processes and have well-structured processes

IAM/GIA, IGA I'm lost in these acronyms!
2 explanations for this ordeal:
- people in IT are in a hurry and no longer have time to speak otherwise. 'Hey, launch the process in the IGA part of the IAM to automate in the ITSM, ASAP! 🙃
- or it encompasses several parts whose specificity we will see 😀
Identity and Access Management (IAM) focuses on managing user access and identities in an IT system, while Identity Governance and Administration (IGA) focuses on managing and monitoring identity and access policies at the enterprise level. IAM and IGA are often used together to ensure centralized and consistent control of access and identities within an enterprise. IAM provides the technical mechanisms to control access, while IGA defines the policies and processes to determine who has access to what, and under what conditions.
IGA is a branch of IAM = the administrative part and not the technical part.
IAM encompasses access to servers and applications, authentication, SSO, MFA, Active Directory administration, web access management, identity federation, and administrative functionalities.

IAM is the invisible part that allows you to set up the main settings; the IGA part is the visible part that allows you to manage automations and connections.
Having only the technical part of IAM risks being very difficult to use without the IGA part.
IAM and IGA make it possible to establish a single repository of identities and a single repository of applications.
GIA is the French translation of IAM: Identity and Access Management.
What are the characteristics of IGA:
I will address this part by including a functioning with an IAM because IGA cannot really function without the structure of identity and access management.
An IGA optimizes the user lifecycle, manages provisionings and deprovisionings, and highlights security flaws.
For this, it is necessary that the solution connects to your different applications and your different HR sources.
Connectors, therefore, play a major role. They allow reading and writing (depending on their configuration, sometimes only reading) of configuration information in applications so that users have access to the correct functionalities with the correct rights.
An IGA solution in addition to an IAM is there to ensure process automation, reliability of actions and information.
When the HRIS (or HR source) and all connectors (AD or user directory, Microsoft 365, Google Workspace, Exchange, Salesforce, etc.) perform bidirectional information exchanges with the IGA solution, this centralizes account, user, and application information.

When we talk about bidirectional exchange, it means that the solution allows for account provisioning upon arrival and account deprovisioning upon departure.
Cross-referencing HR and IT information allows for the establishment of a single user repository and a single account repository.
The benefit of IGA is to automate these actions of centralization and cross-referencing of information. Subsequently, when everything is properly set up, we can move on to the workflow stage to create sequences of actions in an onboarding or offboarding context.
What functionalities can be found in an identity governance and administration tool?
The main features of an Identity Governance and Administration tool are:
- alignment verification
- account review
- highlighting errors or anomalies
- highlighting unused licenses
- entitlement management
- visibility of histories and logs of provisionings and deprovisionings (and other account modifications)
These features are of great interest because they allow to:
- manage the user lifecycle: arrival, movement, departure
- Continuously visualize the adequacy of job role ↔ security group
- find in a user file all the accesses granted and the applications attached to a user
- provide satisfaction to employees who have the right access, from the moment they arrive
- achieve a gain in time and a reduction in the mental load for HR and IT
- Having a better understanding of the workforce at any given time
- Manage licenses more precisely by identifying which ones are in use and which are not.
- know all the accounts present in the IS (active and suspended)
What advantages does an IGA system have on company security?
Companies are required to have a high-performance information system that complies with legal obligations (internal control procedures, GDPR), with a secure, available, and reliable IS.
To ensure security, the company must control access rights management and authorization management, among other things.
For this, an account review must be carried out; this review consists of reconciling users with their accounts. This implies a cross-check of all HR sources and users in the first instance. Attention should be paid to ongoing movements (arrival, departure, job change).
Then, secondly, all the accounts will need to be extracted and linked to the users.
There will be a deduplication effort to be carried out and suspension/deletion of accounts for departed users.
By the time this work is completed, the result will already be obsolete, as user movements, provisioning, and deprovisioning will have occurred.

An IGA and an IAM have the advantage of automating HR/IT synchronizations and providing an immediate account review.
Security groups are defined in AD and imported into the IGA solution, allowing for alignment verification.
The system must also be able to manage the temporary allocation of rights. This will prevent the creation of security vulnerabilities in the event of granting temporary rights or access.
Other points that facilitate the security management of the information system:
- Restrict access to AD. When using an IGA system, the IT department can restrict access to Active Directory to only those who need it, since account creation and suspension are automated.
- Restrict access to the IGA solution. Access can be finely configured, and access can be granted to HR, managers, and the IT department. Access can be granted for the creation of certain accounts or only the reading or validation of access requests or even full access to all functionalities.
- Limit security groups. The proliferation of security groups makes them difficult to manage in the long run. You may want to limit the creation of security groups and 'force' the people in charge of creating accounts to choose from a group list.
In summary
An Identity Governance and Administration system coupled with a more global Identity and Access Management system will ensure several crucial points for the company and ensure its security.
IGA will truly be the visible overlay, but it needs its invisible underlay that will allow synchronization between HR data and IT data necessary for the automation of provisioning and deprovisioning.
An IGA system should help you in your daily management; ease of use should be a central element.





