💡 : It is possible to listen to this article! Find the audio at the bottom of the page 🎧
This injunction may be surprising, but in the banking sector, it is well known:
"know your customer", or KYC for short.
This is a procedure that allows banks to know the identity of their customers in order to comply with current regulations.
Due to the current context, the bank must limit its exposure to risks caused by its customers.
Banks must collect information relating to the legal entity and the natural person, such as identity, source of funds, political connections, etc.
The higher the risk, the more thorough the monitoring and verification will be.
Once the operation is complete, all of this is kept in a folder to prove compliance.
So far, everyone agrees that it is normal for a bank to know its customers, but let's go further, KYC, yes, but why? Why is it necessary to know your customers?
This question may seem amusing, but you will see that it is not as naive as it seems.
Know your customer in the banking sector
The Know Your Customer procedure comes from the European directive in the fight against money laundering and terrorist financing.
KYC was implemented to assess the risk of a business relationship with each client. This procedure is therefore essential in the banking sector, and if banks do not comply with the procedure, they are exposed to sanctions.

To answer my question, why is it necessary to know your customers:
- to avoid financing terrorism
- to avoid participating in money laundering
indirectly:
- to be compliant with the States
What if KYC were a mandatory procedure within companies?
Yes, it makes a lot of sense when you look at the application and the reasons for this procedure in the banking sector, and it is entirely transposable to all companies.
Know your user (KYU) in IT
We transpose everything we have just said from the banking sector to the IT department:
- Due to the current context of cyberattacks, companies must limit their exposure to risks caused by their users. 💡
- Companies must collect information relating to natural persons such as their identity and contractual information.
- The higher the risk, the more important the checks must be, such as past employment if the person works in a sensitive sector or if they are in a management position or with administrator access.
- All of this must be reviewed regularly.
Why know your users?
- to avoid the risk of cyberattacks (from the employee or as part of an external attack)
- to track the user lifecycle
- to apply the principle of least privilege
From this, we are perplexed. This is a fully justified requirement in banking but not at all for the corporate world, yet the risks in both cases are enormous.
The bank has few errors due to this procedure; for companies, it's a different story... attacks exploiting vulnerabilities around users are extremely frequent.

What is a user?
Back to the basic: a user should be seen as a physical person who has a contractual link with the company and not as a computer account.
One person = one user
A user can have multiple accounts. Therefore, one account ≠ one user.
An account is a digital representation of the user in the information system.
⚠️ Don't confuse Active Directory with HR truth!
These are the contracts that link a user to the company.
⚠️ if a user has no contractual relationship, then he or she is not required to have access to the company's IS.
Now that these clarifications have been made, let's see what is complex in the application of KYU in IT.
Why is it so complicated to know your users?
To know your users well, you need several pieces of information such as:
- contractual information
- The contract start and end date (the end date is contract-related and therefore often unknown when the employee arrives).
- operational information such as the necessary accounts, the access that the user should have
This data is essential for creating accounts for the new user. The settings for each account can only be made if the previous information has been refined.
Thus, a matrix of converting employees into accounts can be viewed as follows:
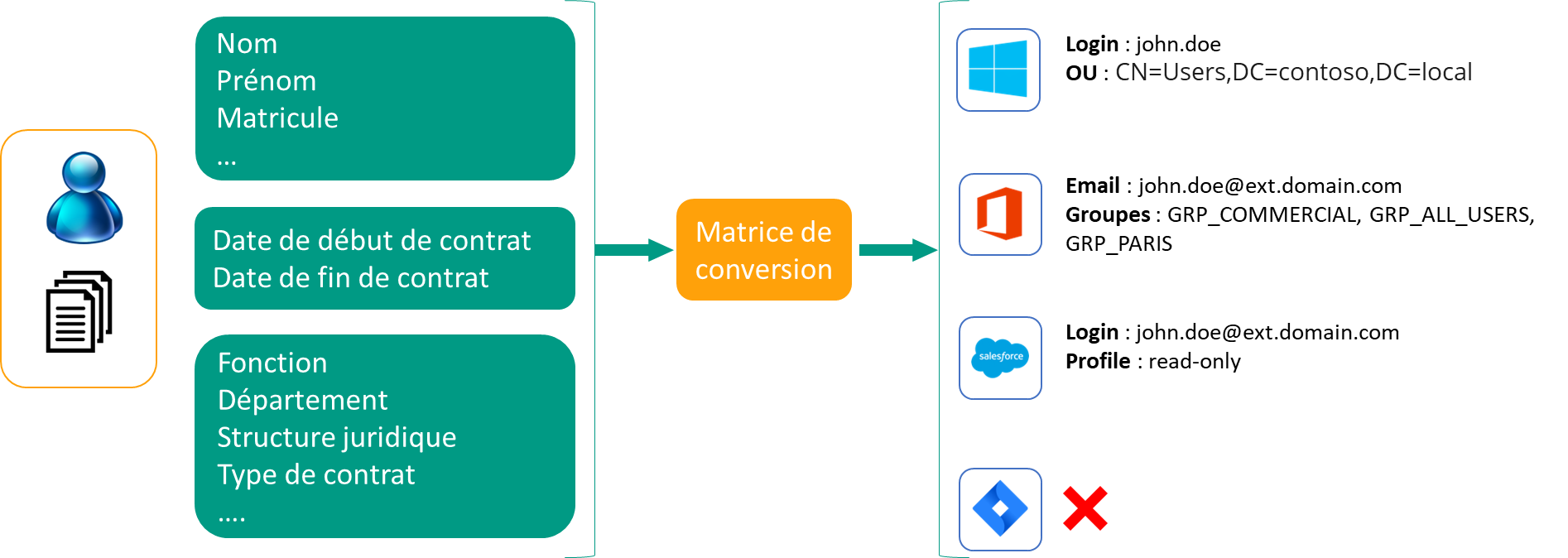
The drawback is that in reality, things get complicated.
The information is scattered across multiple sources.
Where to find employees' administrative information?
The payroll tool is a good source of information for finding employees, except for interns, for example, who are there for less than 2 months because they are not in the tool. The same applies to external service providers who are not in the payroll tool.
Sometimes, the business ERP allows you to list contractors and temporary staff.
Otherwise, there might be a file managed by the manager(s), but that file needs to be up to date.
Employees can also be found on a leave tracking database, but again, this only concerns permanent and fixed-term contracts.
The HRIS is (always) often behind 🫣
The HRIS is always behind, and for good reason: payroll arrives at the end of the month, and the user is only entered on the 20th of the month!
The user does not exist beforehand. Therefore, we cannot anticipate their arrival. To overcome this problem, HR often has an Excel file for new arrivals.
By combining the payroll tool + the file, we arrive at a fairly accurate reference.
A user with multiple contracts
Sometimes a user can accumulate several contracts within a company. This can be the case, for example, with firefighters who may be volunteer firefighters and secretaries. We then end up with two contracts but one person. One user but multiple accesses.
There is also another situation with a user who has multiple contracts. They start as an intern and then finish their internship with a proposal for a fixed-term contract. The budget is there and so are the skills, so they are converted to a permanent contract.
Thus, we have one person and three contracts. One user, but access rights that can become increasingly elevated and numerous.
And lastly, our hero, who juggles several contracts at the same time and has contiguous contracts. 💪

User movements every day
We will create an Excel file to track all these movements (arrival, internal mobility and departure).
How do we proceed? We take all the available information (Excel file from HR, managers, the HRIS and the user directory) and spend a good amount of time creating a single user repository and knowing who is present, with which contract, which applications and which accesses.
However, in the meantime, there have been changes, new users, modifications to departure or arrival dates, service modifications 🤯

Not all information is available
Even if we sometimes try, the information doesn't exist anywhere, so it's impossible to invent it.
If there is no monitoring for service providers or interns, it will not be possible to have a centralized repository.
Service contracts are often managed directly by managers and often on a just-in-time basis, which makes the possibility of a common and properly maintained file very difficult.
What solution is there for better understanding your users?
At this stage, we come to the conclusion that to better understand our users, we need two things:
- thoroughness
- a single user repository
List
Let's list the different types of collaborators that may be present in a company and where we can find reliable information to identify them:
- internal employees: HR department (HRIS or Excel file)
- interns: HR department (excluding HRIS, therefore probably an Excel file)
- temporary staff: managers
List
Next, let's go back to our basic KYU request, what information do I need to properly identify them in my IS?
Be meticulous in this process. If you aim too broadly ('you can never be too careful'), you risk wasting everyone's time. Categorizing each element, finding all the information, the risk of demotivation if there is too much information to fill in will compromise your work, and your repository may quickly fall apart.
Not enough information and you're off hunting for information and so there, once again, no one wins.
Automate
You know as well as I do that any manual action is coupled with a risk of error, omission, and laziness. It is a mental burden, an effort, and a significant risk of error.
Once you have identified all your sources, you need to automate their import to have only one file.
Process
At that point, you have a raw, unprocessed file with duplicates, homonyms, and specific characteristics.

Good news, there is a solution that allows you to perform all these actions, it is an IAM, Identity and Access Management solution. As its name suggests, it manages user identities and access.
At Youzer, we have taken into account all these specific contract types, different sources, and even the absence of a source to assist you in your efforts so that you only have one clean file that will be your single source of truth for users.
How does it work? Youzer retrieves information from your HRIS and transcribes it for account creation. A highly customizable form allows you to centralize and standardize information about new employees who are not in the HRIS. All this information is centralized within Youzer, so you can work on a reliable user base in real time.
Youzer is your know your user!
In conclusion, it is possible to know your users and have a clean file manually, but this implies a lot of rigor and despite everything, risks of errors.
This is not an action that you can carry out whenever you feel like it, as it will take up a significant amount of human resources.
The benefit of automating this action is the reliability of your results and a considerable saving of time. Your user file is always up to date.





