
Hello ️🌼,
I'll see you again for the November edition of Récap'IT.
This month, I take a clear look at the big picture: attacks are accelerating, NIS 2 is stalling,identity plays a central role, and privilege management is too often neglected. Between shocking figures, feedback from the field, and immediately actionable best practices, one question dominates: how can we maintain control in an environment that is spiraling out of control? Enjoy the read.
Enjoy your reading!
📅 Today's agenda:
👉 Go !!
Before we start, I invite you to follow us 👉️
One trend continues unabated: October and November confirmed that cyberattacks are continuing to rise, with no sign of leveling off.
The Check Point Research report shows 1,938 attacks per week per organization, up 5% year-on-year, driven by an explosion in ransomware (+48% reported incidents). The use of GenAI further amplifies the problem: 1 in 44 queries issued from a corporate network presents a high risk of data leakage. The massive deployment of these tools is outpacing the ability of teams to manage them, and the areas of exposure are multiplying.
For its part, Hornetsecurity's annual study shows the same upward trend: 24% of organizations were affected by ransomware in 2025, compared to 18.6% the previous year. Techniques are becoming more sophisticated: AI-powered phishing, compromised terminals, stolen credentials... And despite this, nearly half of CISOs acknowledge that their internal training remains insufficient.
Two studies, one message: volume is increasing, sophistication is increasing, and attackers are automating faster than defense teams can reorganize. A tense final quarter, where CIOs must deal with a reality that has become structural: more AI to produce, more AI to attack, and less room for maneuver.
Source: Hornet Security, Global Security Mag

Receive the best IT news of the month.
Market trends, IT trends, cyberattacks in France... a summary of the news
One year on, NIS2 is progressing... but much slower than expected. In France, transposition has still not been finalized, leaving companies in a regulatory gray area that is slowing down investment while threats continue to rise. And the gap between requirements and reality remains glaring: 1 in 2 employees does not regularly undergo cybersecurity training. Obligations are stepping up a notch, but the security culture is still not keeping pace.
The expansion of the scope adds additional pressure, especially for SMEs that understand the framework but lack the resources to implement it. As a result, compliance becomes a defensive reflex, when the focus should be on resilience.
However, NIS2 did have one merit: it put cybersecurity back at the top of the agenda and strengthened dialogue between the public and private sectors. One major problem remains: overly disparate national approaches, which risk fragmenting European security. Rapid clarification, increased continuing education, and integration of new threats—particularly those related to AI—will be essential to transforming NIS2 into a lever for lasting trust.
Source: Forbes


A clear shift is taking place: in 2026,identity the true perimeter of security. The network has lost all relevance, SaaS chains have expanded at a speed that is impossible to map, and AI now allows attackers to explore vulnerabilities in seconds. In this fragmented environment, the only stable point remainsidentity who accesses what, when, and under what conditions.
The most mature organizations are moving away from total prevention in favor of detection speed, visibility, and fine-grained access control. Single sign-on is becoming an essential standard; transparency on admin accounts is a minimum requirement; and the planned disappearance of passwords is simply a matter of timing. On paper, everything is ready. In practice, however, there remains a considerable gap between available technologies and their implementation.
The year 2026 will see two distinct categories of companies: those that have made identity management the starting point for their security—widespread SSO, controlled lifecycle, SaaS access control, adoption of passwordless approaches—and those that continue to secure a perimeter that no longer exists.
Source: ITPro

Would you like to receive our white paper on identity and access management?

The figures speak for themselves: in France, the most commonly used passwords remain "admin," "123456," and "password." And despite the cosmetic addition of a few special characters, nothing really changes: 80% of data leaks still come from weak or reused passwords. The study points to a surprising but revealing phenomenon: young adults are adopting the same bad practices as their elders. Whether you're 18 or 80, number sequences remain the most common reflex. As long as authentication is based primarily on passwords, attackers won't have to break the lock: they just need to try the classics. The lack of change is such that the transition to more robust mechanisms—access keys, biometrics, device authentication—is now becoming an urgent necessity rather than a trend.
Source: 01net


The Capita case illustrates this once again: negligence no longer has a place—and being a giant in the sector no longer protects you from anything. The UK's largest digital services provider has just been fined £14 million for basic failures: lack of measures to prevent privilege escalation, undetected lateral movement, ignored alerts... As a result, the data of more than 6 million people has been compromised, including critical financial information.
The UK regulator was clear: the incident was not due to the sophistication of the attackers, but to Capita's inability to control its internal privileges and access. This sanction serves as a reminder that the first breach is often found in overly broad rights and insufficient monitoring — not in the technology itself.
Source: Techradar pro


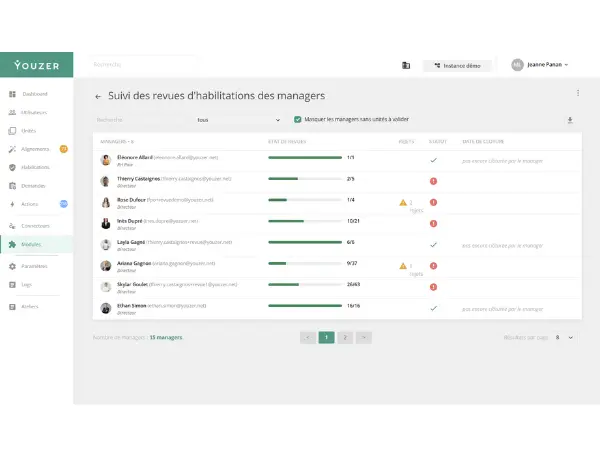
Reviewing permissions remains one of the most effective ways to avoid accumulated rights, forgotten accounts, and overly broad access. The exercise is simple to carry out once it is structured:
In a recent case, a company validated 11,000 accounts, mobilized 1,700 managers, and covered 15 applications in just a few days. A well-conducted review allows you to clean up access without getting bogged down in a cumbersome or time-consuming project.

Thank you for reading me this far!
Any feedback, want to discuss a project?
I'm here for that 👋.
Sharing this newsletter is what keeps it alive!
What if IAM finally stopped being a cumbersome project and became a fast, sovereign strategic lever? This article shows why this change is already underway—and why it will redefine your identity governance.
The CEO of Youzer gives his opinion.
Every month I send you my discoveries, my analysis on IT news.
I do a lot of monitoring and I share it all!
I'm Mélanie and I'm Youzer's marketing manager.
About me? I have an unquenchable thirst for learning! I'd rather read a book 100 times than watch a movie. I'm a fan of HP 🧙🏼.
I do running and collective sport roller (don't look for it, it's dangerous).