
Hello ️✨,
I'll see you again for the January edition of Récap'IT.
To kick off the year, I'm offering you lots of recaps and major trends.
Cybersecurity and IT are entering a decisive phase. Between the government's 2026–2030 cybersecurity strategy, feedback from Clusif, signals from CIOs and CISOs, and reminders from the CNIL, a clear trend is emerging: less talk, more focus on execution. Business continuity, resilience, governance, automation, and IT value are now inseparable.
This edition looks back at the key events and fundamental principles that should not be overlooked.
Enjoy your reading!
📅 Today's agenda:
the government's 2026-30 cyber plan
👉 Go !!
Before we start, I invite you to follow us 👉️

Cybersecurity is no longer a theoretical risk or a subject reserved for specialists. Massive attacks, paralysis of essential services, poorly controlled digital dependencies: cyber has become part of everyday economic and political life. It is in this context that the government is setting its course for the period 2026–2030, with a clear ambition: to strengthen the country's ability to withstand major cyber shocks and continue to function. Six key guidelines emerge from this strategy.
Essentially, the government is no longer seeking to patch up isolated flaws, but to build long-term resilience in a cyberspace that is now inherently conflictual. The approach is coherent: talent, regulation, industry, crisis management, and cooperation are considered as a whole, a sign that cyber security is now treated as a strategic issue in its own right. The strongest signal remains the shift towards business continuity and crisis management: the possibility of major attacks is no longer theoretical, but has become a baseline scenario. A delicate balance remains: raising the bar without disrupting an economic fabric that is highly uneven in terms of cyber maturity. The focus on the cloud, the software chain, and post-quantum cryptography is a step in the right direction, but it requires profound transformations. Clearly, the intention is there; it is the execution, in the field, that will determine whether this strategy delivers on its promises.
Source: SGDSN Government


Receive the best IT news of the month.
Market trends, IT trends, cyberattacks in France... a summary of the news
In 2026, CIOs are operating under pressure: cyber threats are on the rise, budgets are tight, and business expectations are higher than ever.
Abraxio's Panorama 2026, an annual barometer based on feedback from several hundred CIOs and IT managers, highlights six priorities that reflect the changing role of IT departments: ensuring a reliable IT system while contributing to value creation.
Source: ITpro


The CESIN 2025 barometer, based on feedback from CISOs and cyber directors and focused on incidents with real impact, paints a clear picture: significant attacks are declining, but their consequences remain major. Forty percent of companies have been affected, and in nearly eight out of ten cases, the impact is direct on the business, image, or data. Cybersecurity is no longer about the volume of alerts blocked, but about the ability to contain the incident, react quickly, and regain control of operations.
The threat is changing as a result of the geopolitical context. More than half of companies are seeing an increase in state-sponsored attacks, and 40% consider cyber espionage to be a high risk. Digital sovereignty is emerging as a risk management issue, particularly in relation to the cloud, contractual dependencies, and third-party risk, which is now identified as a major vector for incidents.
Finally, organizations are maturing. Security fundamentals are widely deployed, visibility into assets is improving, and cybersecurity is fully integrated into governance: 92% of companies rank it among their top five risks. Budgets are stabilizing, marking a phase of consolidation rather than withdrawal.
This barometer sends a clear signal: faced with more targeted and interconnected threats, the challenge is no longer to multiply solutions, but to sustainably strengthen companies' ability to anticipate, contain, and manage cyber risk.
Source: CESIN


The data leak affecting BreachForums in early 2026 serves as a reminder of a fundamental reality: no platform is immune to compromise. Even a forum designed for anonymous exchanges between cybercriminals remains exposed when it hosts sensitive data and identities.
BreachForums has established itself as a central hub for the underground, used to share stolen data and illicit tools. Its appeal lies in the anonymity and discretion of its exchanges. The exposure of its user base shows that this appeal depends as much on internal practices as on technical choices.
The incident highlights a key point: securing an anonymous exchange platform is inherently complex. The slightest weakness in infrastructure or data management turns the service into a leak point, even for users who are aware of digital risks.
Beyond the symbolism, BreachForums reminds us that anonymity
is never guaranteed. Any platform that concentrates sensitive data becomes a potential target, regardless of its level of expertise or positioning.
Source: Digital Solutions

Would you like to receive our white paper on identity and access management?

The €42 million fine imposed on Free and Free Mobile sends a strong message. For the CNIL, the October 2024 attack was not an isolated incident but a poorly anticipated risk. Security measures deemed insufficient led to the compromise of data from 24 million contracts, with direct impacts for subscribers.
This decision confirms a clear shift in regulatory interpretation. Cyberattacks are now considered an ongoing risk that organizations must incorporate into their normal operations. Failure to do so exposes them to heavy penalties, regardless of the status or size of the entity concerned.
Source: Silicon
.webp)

Listening to the Clusif annual conference dedicated to feedback from 2025, one thing quickly becomes clear: cyber has changed in nature. Attacks are no longer limited to data theft or temporary IT system interruptions; they now have a concrete impact on everyday life—transportation at a standstill, production lines halted, supply chain disruptions, essential services disrupted. Speakers demonstrated this through numerous examples: critical infrastructure, logistics, industry, distribution, and public services have become obvious targets, sometimes for clearly geopolitical reasons.
Another key lesson learned over the past year is that the methods used remain surprisingly simple: phishing, social engineering, compromising subcontractors, and weak credentials continue to open the door to the most costly attacks.
The CNIL has made it clear: despite the apparent sophistication of campaigns, the breaches observed are often basic and therefore difficult to excuse. Implicitly, 2025 confirms that cybersecurity is no longer an isolated technical issue, but a direct factor in economic continuity, trust, and collective stability.
Source: Clusif


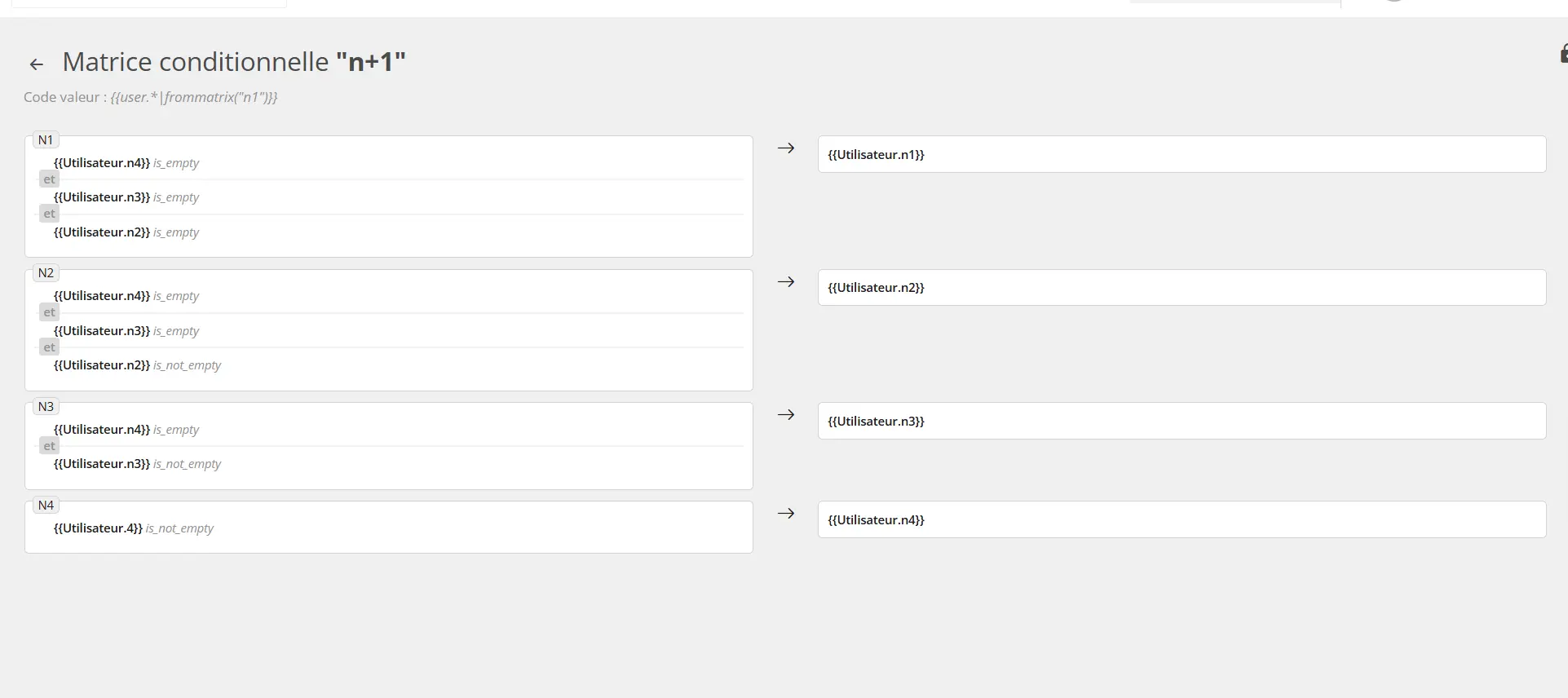
It is sometimes difficult for organizations to have a workable view of the entire hierarchical chain.
HR sources often contain several levels of management, but this information remains complex to exploit directly in operational tools. The approach presented by Youzer consists of using correspondence tables to obtain all hierarchical levels within user records in order to finally make this data actionable. This makes it possible to:
This feedback clearly illustrates the added value of automation and visualization: without this type of approach, the information exists but remains difficult to use; with it, it becomes an operational lever that can be immediately used by IT and business teams.
Thank you for reading me this far!
Any feedback, want to discuss a project?
I'm here for that 👋.
We've sent you the newsletter and you think it's great? Sign up here 👇
Sharing this newsletter is what keeps it alive!
Every month I send you my discoveries, my analysis on IT news.
I do a lot of monitoring and I share it all!
I'm Mélanie and I'm Youzer's marketing manager.
About me? I have an unquenchable thirst for learning! I'd rather read a book 100 times than watch a movie. I'm a fan of HP 🧙🏼.
I do running and collective sport roller (don't look for it, it's dangerous).