
Hello ️🌼,
Welcome back to the March edition of Récap'IT. In 2025, cybersecurity leaves no room for improvisation. Between the rise of cyber defense exercises such as DEFNET, a flood of regulations with NIS 2, DORA, and the Cyber Resilience Act, and increasingly targeted threats to critical infrastructure—particularly Active Directory—CIOs and CISOs are navigating a minefield.
Good news: the 2024 indicators also show signs of maturity. In this edition, I offer an overview of the major trends, costly oversights, and weak signals that should not be ignored.
📅 Today's agenda:

👉 Go !!
Before we start, I invite you to follow us 👉️

Simulate an attack on critical military systems. Test coordination between 15 entities within the Department of Defense. Immerse 1,400 cyber warriors in realistic scenarios combining intrusion, disinformation, and infrastructure paralysis. That's DEFNET.
Held from March 17 to 28 in Rennes, DEFNET 2025 is the benchmark joint military exercise in cyber defense. More than just training, it is a full-scale stress test of France's capabilities in the face of digital threats. The objective is to prepare the armed forces to deal with defensive cyber warfare and influence attacks in a context of increasingly likely hybrid conflicts.
The format is evolving: alongside the armed forces, cybersecurity students, industry representatives, and civilian partners have been integrated into the exercise. Rennes, with its Cyber Excellence Center, is playing a greater role than ever as a national hub.
Another highlight of this edition was the involvement of the cyber operational reserve. These specialists, who can be mobilized in the event of a crisis, strengthen the system and herald a more distributed approach to cyber defense—one that can adapt quickly across the entire country.
DEFNET 2025 does not seek to educate. It aims to confront teams with complexity, uncertainty, and information overload. Because in digital warfare, coordination, speed, and resilience cannot be decreed. They must be built.
Sources: OuestFrance, Ministry of the Armed Forces


Receive the best IT news of the month.
Market trends, IT trends, cyberattacks in France... a summary of the news
NIS 2, DORA, REC... a wave of regulations is sweeping across the French digital ecosystem, directly affecting 15,000 companies. But behind these European acronyms lies a concrete reality: preparing for cyber threats will no longer be a luxury, but an obligation.
This bill, which was reviewed by the Senate on March 11, transposes three major European directives:
NIS 2 extends the scope of cybersecurity to 15,000 entities, up from 300 previously. The goal is to ensure business continuity in the event of an attack by imposing a long-term vision and robust response plans.
REC (Resilience of Critical Entities) targets digital resilience in the face of cyber threats and supply chain disruptions. Suppliers, publishers, distributors: everyone is affected.
DORA, reserved for the financial sector, places digital operational resilience at the heart of regulation.
But the law does not only target large corporations. Start-ups, which are agile but exposed, are on the front line. Some will have to apply the basics (such as protecting themselves against ransomware), while others may be designated if their activity is deemed strategic—even if they do not meet the usual thresholds. A small, innovative lab may be enough to attract attention.
Requirements will be adjusted according to the size and role of the company. ANSSI, which until now has provided technical support, will also become a regulator. Support will be provided in part by private service providers, and regional centers are planned, alongside the Cyber Campus. However, funding remains unclear, which is a cause for concern for organizations with limited resources.
For those who can integrate cybersecurity from the design stage onwards, this is an opportunity to gain the trust of the market and stand out from the crowd. However, the support provided must be adequate. Without concrete resources, this ambition could quickly come up against reality.
Source: Innovations


In its latest threat overview, ANSSI sounds the alarm: bad practices surrounding Active Directory are far too common... and systemic.
The first damning finding: 36% of Windows servers audited are still running an obsolete version (Windows Server 2012 R2 or earlier), even though the Zerologon vulnerability continues to be exploited on outdated domain controllers. Worse still, the agency notes that some privileged account passwords have not been changed in 15 to 25 years. Yes, 25 years. The recommended minimum? A rotation every three years.
Other errors that recur with disconcerting regularity include: Incorrectly positioned SPNs (ServicePrincipalNames) on privileged accounts, opening the door to brute force attacks; incorrectly configured enrollment permissions on certificate templates, allowing malicious users to authenticate to any AD account; and excessive permissions granted to non-privileged accounts, which are then able to modify GPO objects or attack domain controllers.
The verdict is clear: too many organizations have yet to grasp the level of rigor required by Active Directory. Leaving these vulnerabilities unaddressed is tantamount to handing over the keys to the kingdom to the first successful intruder.
Source: Silicon


Companies are responding, but not quickly enough. The Docaposte/Cyblex 2024 barometer shows awareness... but not full maturity.
Attacks up 50% in one year. One-third of companies affected, mainly by phishing, ransomware, and data theft.
4 out of 10 companies feel threatened (+33%). Large mid-sized companies are the most concerned.
72% think they are ready, but 77% do not apply ANSSI's basic practices 🤯.
66% use a specialized service provider (twice as many as in 2023), and 59% have increased their cybersecurity budget.
The public sector is taking the lead: more resources, more compliance, more sovereignty.
Verdict: the cyber reflex is there, but poorly controlled. Protection is improving... on paper.
Source: ITPro

Would you like to receive our white paper on identity and access management?



University of Rennes: the FunkSek hacker group steals 50GB of data and encrypts it.
Autosur: the vehicle inspection company has suffered a cyberattack, with more than 10 million people potentially affected.
La Poste: millions of pieces of data have been stolen. In March, a hacker put a file containing the data of 50,000 French citizens up for sale.
Phishing campaign: Free customers are being targeted by a well-orchestrated scam involving Amazon Prime (data stolen in 2024).
Still Free: the CNIL has launched disciplinary proceedings against the operator.
Harvest: Following a cyberattack against the financial services and wealth management software company, MAIF and BPCE were affected by data leaks.
Intersport: data was stolen and a file containing 3.4 million people was put up for sale.
DDoS attacks: Sopra Steria Group—a French information technology company, Cyanide Studio—a French video game development studio, France Télévisions Publicité, SAFT—an industrial company, Saft4U—a document and services portal, Vinci S.A., Rubis—a French company, supplier of natural gas and petroleum products, CIFFCO – a subsidiary of the Getlink group, the leading private training organization accredited by the EPSF, Microids – a French video game development company.

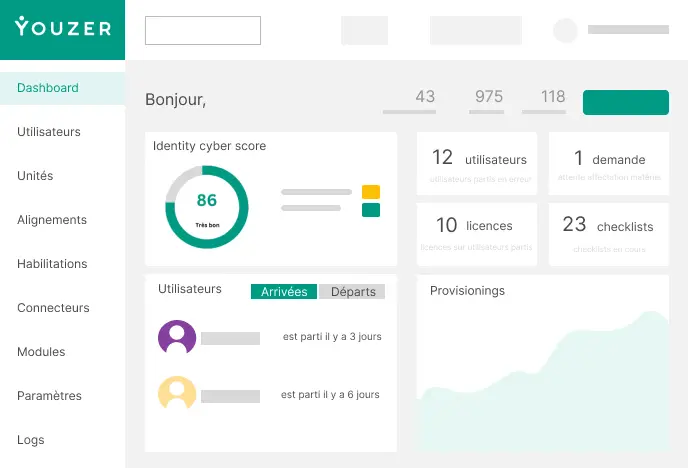
The departure of an employee should never leave any traces in the information system. However, in many organizations, accounts remain active long after the user has left the company. This is a common situation, often invisible, but one that can be costly in terms of unnecessarily consumed licenses, security risks, or regulatory non-compliance.
Without a centralized tool, it is extremely complex to identify these cases. It is necessary to:
Youzer automates this detection.
From the dashboard, you can immediately see which users are in error: those who have left the company but whose one or more units remain active. You can also identify licenses that are still assigned to activated units whose users have left, often resulting in unnecessary billing.
Result:
What Youzer brings you is visibility, rigor, and above all, the certainty that departures are effectively followed by a complete offboarding process.
Would you like to know how many former employees still have access to your company? One demonstration is all it takes.
Thank you for reading me this far!
Any feedback, want to discuss a project?
I'm here for that 👋.
Every month I send you my discoveries, my analysis on IT news.
I do a lot of monitoring and I share it all!
I'm Mélanie and I'm Youzer's marketing manager.
About me? I have an unquenchable thirst for learning! I'd rather read a book 100 times than watch a movie. I'm a fan of HP 🧙🏼.
I do running and collective sport roller (don't look for it, it's dangerous).