
Hello ️✨,
Welcome back to the December edition of the IT Recap.
In this end-of-year edition, I offer an overview of the key developments that marked 2025: the evolution of IAM and application identities, the rise of AI agents, regulatory pressure, feedback from crisis exercises, and decisions by the authorities. These are all topics that are already shaping the IT and cyber priorities for 2026.
Happy reading and happy holidays! 🎉
📅 Today's agenda:
👉 Go !!
Before we begin, I invite you to follow us 👉
️

By 2025, IAM will have clearly changed in scope.
Airitos' Identity & Access Management Trends Report 2025 takes stock of the developments observed throughout the year and highlights several major disruptions that are no longer just theoretical, but operational.
Source: Airitos


Receive the best IT news of the month.
Market trends, IT trends, cyberattacks in France... a summary of the news
The cyber security report for 2025 confirms a now well-established reality: technical sophistication is advancing, but humans remain the preferred entry point for attacks, as demonstrated by several highly targeted social engineering campaigns, particularly in regulated sectors.
At the same time, the widespread adoption of generative AI has opened up new blind spots: a dramatic increase in unregulated use, exposure of sensitive data via consumer tools, and the emergence of attacks that directly exploit models (prompt injection, automated disinformation).
Incidents affecting critical infrastructure and subcontracting chains serve as a reminder that cyber impacts are no longer abstract, but immediately operational.
Finally, 2025 marks a turning point in terms of governance: cyber responsibility clearly falls back to senior management, with mechanisms linking security performance, budgetary decisions, and executive responsibility. This sends a clear message to organizations: cyber resilience now depends as much on human and organizational choices as it does on tools.
Source: computerweekly


At the end of December, the Italian Competition Authority fined Apple €98.6 million for abuse of its dominant position in relation to its App Tracking Transparency (ATT) feature.
At issue: consent rules deemed disproportionate and imposed unilaterally on third-party developers, while Apple's services would benefit from more favorable conditions. Following a similar sanction in France and under the watchful eye of other European regulators, this decision illustrates a growing tension between access governance, user consent, and competitive fairness.
A strong signal for CIOs:identity access control mechanisms are no longer just security or compliance issues, but also fundamental economic and regulatory challenges.
Source: SiècleDigital


Against a backdrop of geopolitical tensions, increased regulatory pressure, and rapid adoption of AI, the new president of Clusif, Odile Duthil, emphasizes a key point: cybersecurity must now be understood and arbitrated at the executive committee level.
The association works to provide concrete guidelines on strategic autonomy, data sensitivity, and hosting choices, far removed from dogmatic discourse. In terms of regulation, NIS 2 is part of a broader framework (DORA, CRA) aimed at raising the overall maturity of organizations and their suppliers, with a strong focus on third-party management and awareness of IT vulnerabilities.
Finally, Clusif warns of the risks associated with generative AI—data leaks, fraud, phishing—while pointing out that it is also becoming a detection tool, and calls for immediate action to anticipate long-term issues such as post-quantum encryption. The message is clear: cybersecurity is no longer an isolated technical issue, but a matter of governance and strategic decision-making.
Source: LeMondeInformatique

Would you like to receive our white paper on identity and access management?

At the end of December, the CNIL imposed a fine of €1.7 million on NEXPUBLICA France for serious breaches of the security obligation set out in Article 32 of the GDPR, concerning software used by public actors in the field of social action. The investigation highlighted a structural weakness in the information system, vulnerabilities relating to basic security principles and, above all, flaws that were known and documented by audits but only corrected after data breaches involving particularly sensitive information.
Beyond the amount of the penalty, this case sends a clear message: for publishers and IT managers alike, failure to fix identified vulnerabilities will no longer be tolerated, and application security is now a matter of compliance and responsibility, including in critical business environments.
Source: CNIL


Rempar is a national cyber crisis exercise organized by ANSSI, designed to test organizations' ability to manage a major cyber incident (which I discussed in the September edition) under real-life conditions.
Feedback from the Rempar25 exercise shows clear progress in the initial technical actions taken in a crisis situation: rapid identification of priorities, containment, and securing of information systems are generally well managed.
However, ANSSI points to persistent shortcomings in critical areas, particularly business continuity, crisis recovery, and anticipation, which are only partially addressed by a significant proportion of participants. The most mature organizations stand out for their clear business continuity plans, which are known to teams and regularly tested, facilitating the rapid mobilization of support functions and management.
Conversely, less prepared organizations still struggle to coordinate the right people at the right time, revealing a gap between technical expertise and overall crisis management. This sends a strong message: cyber resilience is no longer just about the SOC, but about the organization's ability to function under pressure.
Source: Lemondeinformatique


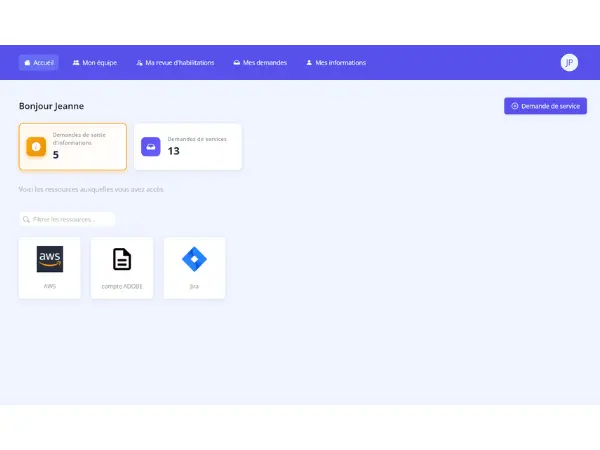
My Youzer is the interface dedicated to end users and managers to simplify day-to-day access management. Each user has a clear view of all the accounts and applications to which they have access, while managers can view their employees' permissions and take direct action on issues that concern them.
In concrete terms, My Youzer allows you to:
Each request is then handled by Youzer App and integrated into a fully configurable validation process: validators receive the request, approve or reject it, and then provisioning is launched manually or automatically. My Youzer thus brings greater fluidity to business operations, while ensuring control, traceability, and governance of access for IT and security teams.
Thank you for reading me this far!
Any feedback, want to discuss a project?
I'm here for that 👋.
👉Reply to this newsletter
We've sent you the newsletter and you think it's great? Sign up here 👇
Sharing this newsletter is what keeps it alive!
Every month I send you my discoveries, my analysis on IT news.
I do a lot of monitoring and I share it all!
I'm Mélanie and I'm Youzer's marketing manager.
About me? I have an unquenchable thirst for learning! I'd rather read a book 100 times than watch a movie. I'm a fan of HP 🧙🏼.
I do running and collective sport roller (don't look for it, it's dangerous).