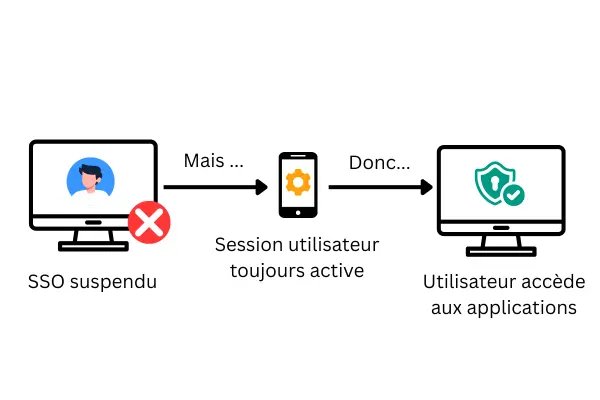
One Friday afternoon, during a routine audit, a CIO came across a chilling detail: a former employee had logged on to a critical application... three days earlier. Problem: this employee had left the company a month earlier, and his main account had been suspended in the SSO.
How is this possible? On cell phones, some sessions remain active indefinitely without going through the SSO again. As a result, the door remains open, even after the employee has left.
There's nothing unusual about this scenario. Many companies think that deploying SSO is the equivalent of securing their identities. In reality, SSO facilitates authentication, but does not manage the account lifecycle. To confuse SSO with IAM is to run the risk of letting critical accesses go out of control.
Why confuse SSO with IAM?
Confusion arises first and foremost from visibility. SSO can be seen and experienced on a daily basis: an employee clicks, enters his password once, and accesses all his applications. This saves time, less forgetting, fewer passwords to manage. For the user, it's tangible and immediate.
IAM, on the other hand, works behind the scenes. It orchestrates the creation and deletion of accounts, adjusts rights according to business roles, and ensures that access follows an employee's lifecycle. This work is invisible to the end-user, but essential for security and compliance.
Added to this is the communication factor. Many software publishers promote SSO as an "identity management solution", creating ambiguity whether intentional or not. This makes it easy for decision-makers to think that implementing SSO is the same as solving the IAM issue.
In reality, SSO addresses an authentication problem. IAM, on the other hand, addresses a problem of identity and access governance. To confuse the two is to treat the visible surface, leaving the depth of the problem untouched.
What SSO really does... and what it doesn't do
Single Sign-On (SSO ) meets a simple need: to facilitate access to applications. In concrete terms, the user authenticates only once with anidentity Provider (IdP), which becomes the point of trust. Once validated, he or she has frictionless access to all connected applications, without having to re-enter his or her credentials.
The appeal is obvious:
- Improved user experience: fewer passwords to remember, fewer failed logins.
- Increased productivity: employees can move quickly between applications.
- Enhanced security: authentication is centralized, enabling the implementation of robust policies (MFA, connection control, logging).
In short, SSO is a bridge between the user and his applications, simplifying authentication and centralizing control.
But this bridge has its limits: it doesn't manage the creation or deletion of accounts in the applications themselves, it doesn't control business roles, and it can be circumvented by persistent sessions (especially on cell phones). In other words, SSO facilitates access... but it doesn't govern identities.
What IAM really covers
Identity and Access Management (IAM) goes far beyond the scope of SSO. Where SSO focuses on authentication, IAM manages the entire identity lifecycle within the information system.
In concrete terms, this covers four key dimensions:
- Identity lifecycle: creation of accounts when an employee joins, updating of rights in the event of internal mobility, automatic deletion on departure.
- Rights governance: align access to business roles, avoid excessive privileges, eliminate orphan accounts.
- Automation: provision the right accesses in minutes rather than hours, make offboarding systematic and reliable.
- Traceability and compliance: prove at any time who has access to what, respond quickly to ISO and RGPD audits.
In practice, IAM does not replace SSO: it complements it. SSO facilitates authentication, while IAM guarantees control and governance.
In practice, IAM does not replace SSO: it complements it. SSO facilitates authentication, while IAM guarantees control and governance. It is the combination of the two that ensures both convenience for users and security for the company.
Differences between SSO & IAM
The real risks of an "SSO only" vision
Reducing access management to SSO alone means treating the symptom without curing the cause. SSO solves an authentication problem; it governs neither identities nor rights. This confusion creates blind spots that end up costing a lot - in security, in operations and in budget.
Firstly, operational risk: a poorly dimensioned SSO becomes a single point of failure. The slightest IdP failure blocks connections and paralyzes business. Conversely, over-hardening (MFA everywhere, controls too strict) without rights governance doesn't correct inappropriate access; it just adds friction.
Then there's the security risk: SSO does not delete or revoke accounts in applications. Persistent sessions (especially mobile ones) and undeprovisioned accounts create ghost accounts. You can suspendidentity on the IdP side and leave doors open on the application side. The result: unnecessary exposure, painful auditing and the inability to quickly prove "who has access to what".
Thirdly, the economic risk: trying to get the same SSO product to do the same work as an IAM leads to vendor dependency and automatically increases costs (licenses, diverted integrations, specific developments, more complex runs). You pay more, without getting the governance you expect.
Fourthly, the organizational risk: SSO is a technical IT project (robustness, availability, security) that can be deployed in just a few weeks. IAM, on the other hand, is an organizational project involving HR, business and security: definition of roles, formalization of on/offboarding processes, controlled delegation, compliance. Traditionally, this type of project takes several months to complete, as it involves changing responsibilities and traceability, far beyond a simple technical connection.
With solutions like Youzer, this implementation can be considerably accelerated, thanks to rapid integration with existing environments and out-of-the-box automation. But this does not dispense with upstream thinking: technology alone does not define business roles or governance processes. It provides the framework for applying them effectively.
Finally, the risk of trajectory: persisting with SSO-only logic delays the implementation of IAM fundamentals (business roles, access review campaigns, segregation of duties). We improve the entrance to the house without checking who holds the keys.
To put it plainly: SSO alone brings convenience and a first layer of security to authentication, but it doesn't prevent excessive rights, orphaned accounts or surviving sessions. Without IAM, you have no control over the identity lifecycle, proof of compliance or rights consistency. The winning combination is a robust SSO... driven by IAM governance that automates, traces and aligns access to business roles, step by step.
How can SSO and IAM be combined effectively?
The right approach is not to choose between SSO and IAM, but to combine them intelligently. SSO streamlines the user experience, while IAM governs access: together, they form a coherent, secure architecture. It's just a question of getting them right.
- Strengthen SSO authentication. Centralized entry is useful, but insufficient if it remains vulnerable. Generalizing MFA, or even contextual authentication (based on the device or location of connection), can greatly reduce the risk of compromise.
- Connect SSO to an IAM brick capable of managing the complete identity lifecycle. IAM must control the creation and deletion of accounts in applications, based on HR data and business roles. This ensures that rights automatically follow an employee's development - and disappear when he or she leaves.
- Apply continuous governance: conduct access review campaigns, apply the principle of least privilege and regularly adjust policies. This is not a project that you "install once", but a living mechanism.
- Take care of the user experience. Too much friction and the system will be bypassed. A good balance combines the simplicity of SSO (a single, fluid authentication) with the rigor of IAM (accurate rights and traceability).
Solutions such as Youzer provide a pragmatic way of achieving this: rapidly integrating cloud and on-premise applications, automating on/offboarding and delegating certain actions to managers, while maintaining full traceability. IT takes back control, without unnecessary complexity.
Conclusion
SSO alone is not an IAM strategy. It's a comfortable shortcut, but a dangerous one. SSO provides fluid, centralized authentication, but does not govern identities or rights. Confusing the two leaves the door open to phantom accounts, persistent sessions and excessive rights.
The message is clear: SSO and IAM complement each other, and it's only by working together that user comfort, security and compliance can be reconciled.
The real question for a company or organization is therefore not "do I have an SSO?", but "do I have proof that my identities are under control from end to end?". And this proof can be measured: onboarding time reduced from several hours to a few minutes, percentage of accounts actually deactivated when an employee leaves, ability to respond in record time during an RGPD audit.
It's this transition from feelings to concrete indicators that lends credibility to the IT department's and CISO's actions - and distinguishes a simple comfort tool (SSO) from genuine access governance (IAM).





